Hosted OpenID Connect (OIDC) user journeys to reduce time-to-market
Deprecation NoticeThe content on this page has been deprecated and is no longer valid. We have made significant improvements and updates to provide you with the most accurate and up-to-date information.
To access the latest content, please visit: Hosted Journeys.
Next Identity Journeys deliver hosted pre-registration, registration, login, forgot password, profile, and other common customer use cases with industry standard Open ID Connect (OIDC) integration patterns. Deploy fast, save money, follow industry best practices, achieve security and privacy requirements, and stay on the cutting edge across your global customer identity landscape.
Follow the documentation in this section to integrate Next Identity Hosted Journeys with your applications.
Protected by Threat GuardNext Identity Journeys includes Threat Guard to protect your customers and your brand.
Invite customers to your application via activation journeys designed to control access to your application while providing customers the opportunity to complete their profile after receiving an invitation via email or SMS.
About inviting or pre-registering users for Hosted Journeys integrationsPre-registering and activating new users where self-registration is disabled requires an API call to the Journeys API
/pre-registerendpoint.
Provide your customers with a fully self-service registration option. Collect as much or as little info as you need during the registration process, determine the authentication options, suggest or enforce 2-step verification and make sure your customers have verified their method of authentication during the registration journey by sending them an email or SMS with a code or link to complete their registration.
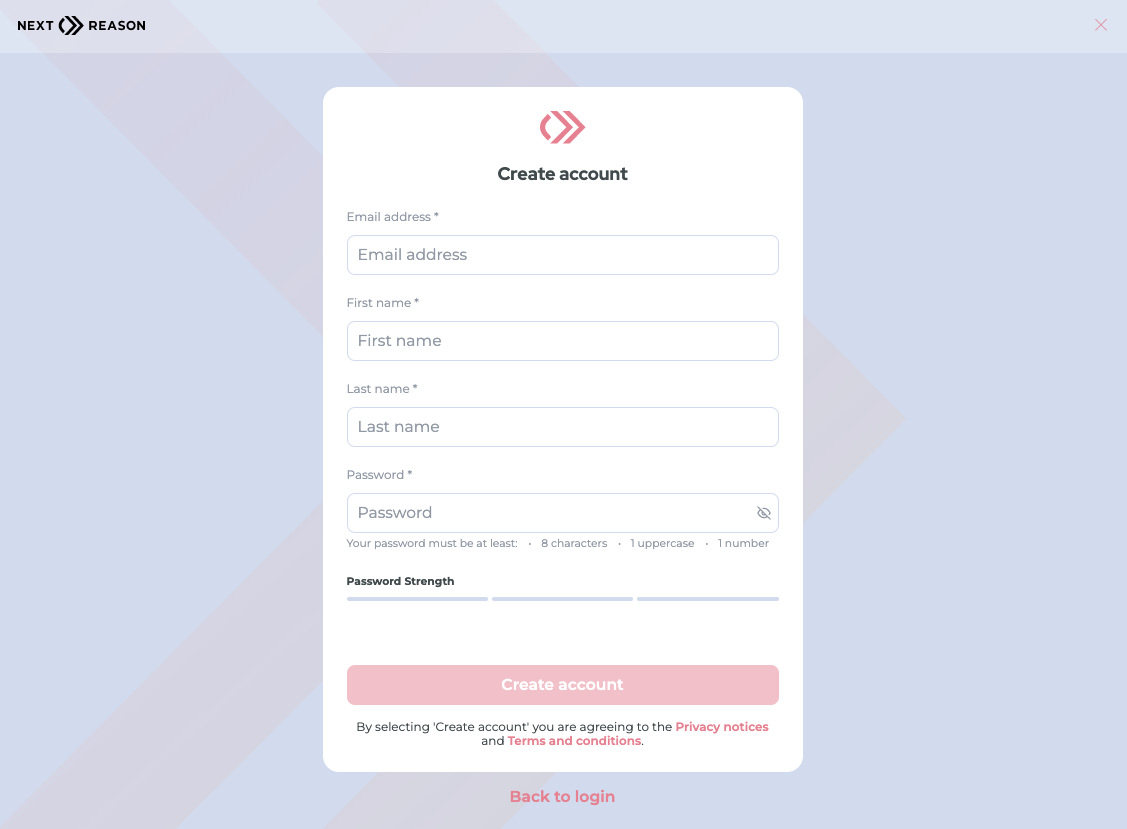
Support multiple login methods depending on your application's requirements including email and password, mobile phone number and password, passwordless options including biometric authentication. Protect your customers and your brand against credential stuffing attacks with form security from Threat Guard.
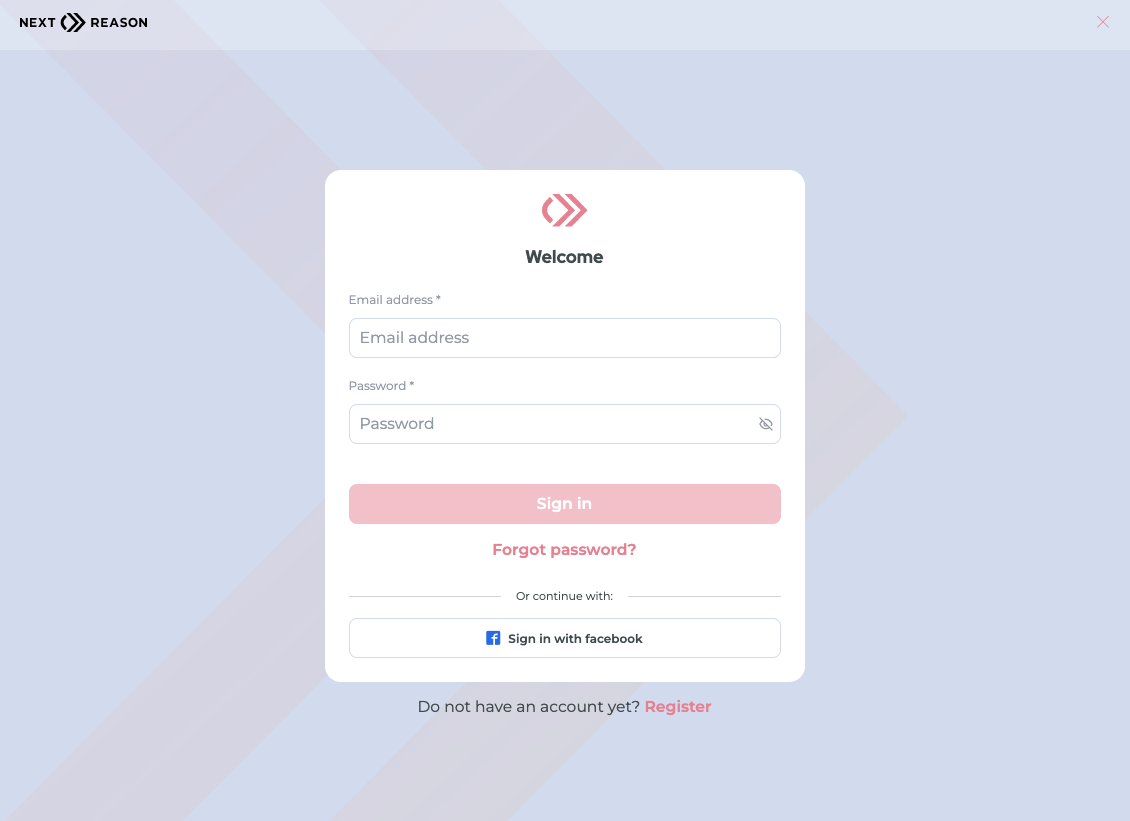
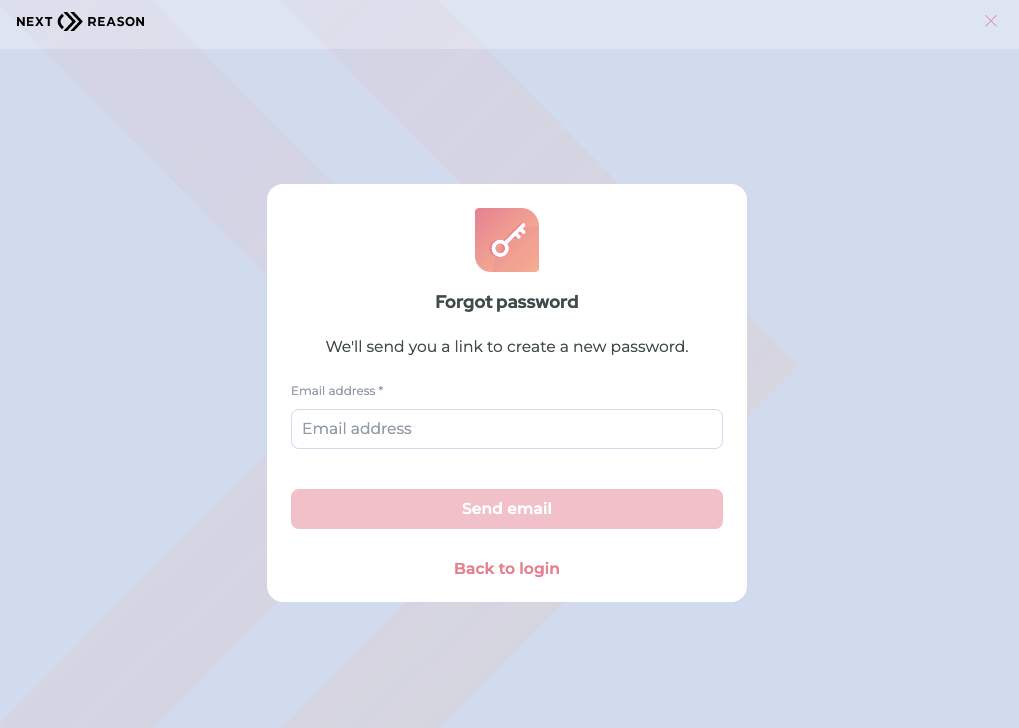
Reduce calls and support requests from your customers by offering self-service options to reset their password and to have a "magic link" sent to them if they forget their password.
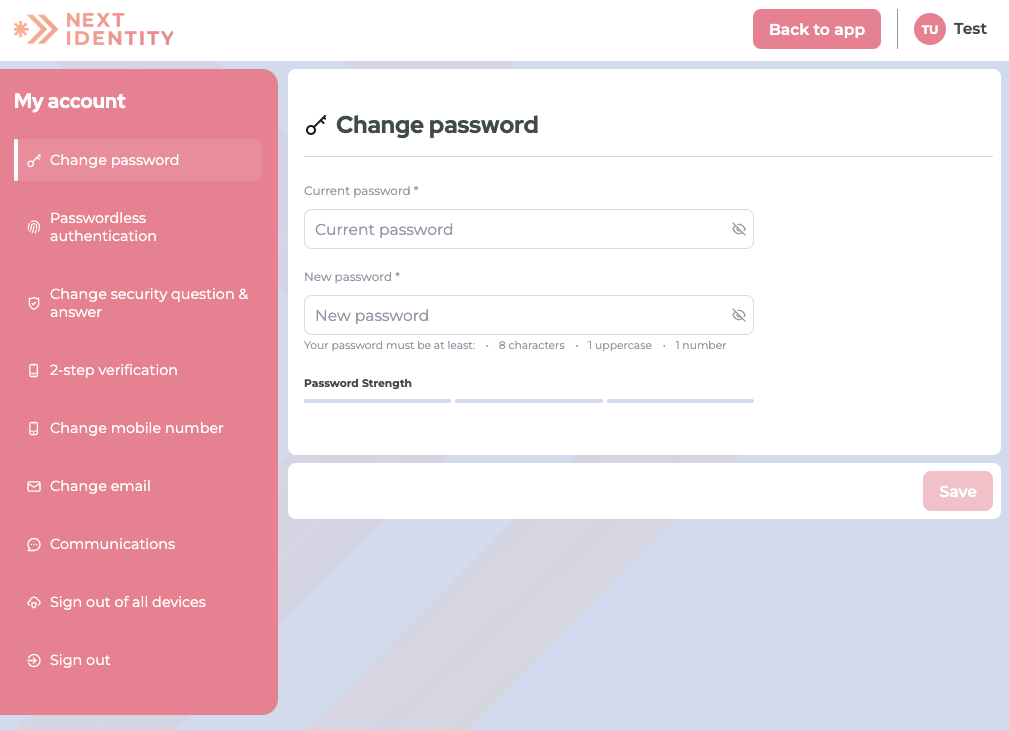
Enable customers to update their own profile including changing their email address or phone number, update their mailing address or communication preferences, or any editing other profile attribute you collect.
The code-for-token exchange will often be the second step in your integration with Next Identity Journeys. In this step, the user has already been redirected back to your application after successful registration or sign in, and the redirect URL will contain an authorization code parameter.
Retrieve data from a user's profile with a valid access token.
The discovery document, also referred to as the "well-known endpoint," contains OpenID Connect values that can be retrieved by OIDC clients. The discovery document enables OIDC clients to configure themselves in order to be able to access your implementation of Next Identity.
Give customers control over access to their account by enabling them to end their session and sign out of active sessions on all devices.
