Consumer Access Control
Ensuring end users have control over their online accounts is a core focus of the Next Identity platform. Enterprise organizations can help build trust with their valued customers and B2B users by allowing users to grant and revoke access to an application.
For many global organizations with an identity solution deployed across dozens or even hundreds of distinct applications, the granular management of user access can be complicated and hard to manage. Next Identity’s Consumer Access Control feature provides a unified view of the user at the organization level and allows the end user to individually grant and revoke access to specific properties within the organization.
PrerequisiteConsumer access control is available to any applications that are using the Next Identity token delegation service.
What is a property?
Consumer Access Control introduces the concept of a “property” to the service. A property is an identifier that can be assigned to one or more end-user-facing applications within the Next Identity service. Each organization using the Next Identity service can define its own property groupings. A typical property grouping might consist of all sites within a sub-brand of an organization or all applications within a specific region, or an organization may choose to define each integration with the Next Identity as an individual property.
Your Next Identity onboarding consultant can help advise your team on property groupings that would be the most useful for your organization and end-user needs.
How does consumer access control work?
Next Identity provides granular access control for an end user across each property within an organization.
When an end user creates an account, logs in, or is pre-registered for an application, the consumer access control service is invoked. Based on policies set by the organization, an end user new to a property will either be asked to provide consent for access to a property or the consent will be granted implicitly. An existing end user who signs in to an application will have their access status checked upon login to determine if access to that property is granted or if it has been revoked.
How is consumer access managed?
There are three methods to manage user access.
-
The user can manage their own access from the personal details page on the hosted journeys,
-
The user can manage their own access from a custom page built by an API-integrated application,
-
An application admin can submit a revoke access request on behalf of the user via API call.
Managing consumer access with hosted journeys
After login, Next Identity hosted journeys provide a user interface that allows an end user to manage their access status for the property actively and immediately revoke access if desired.
To manage access, a logged-in consumer can navigate to the personal details screen and revoke access from the current application. If users revoke their access from an application, their session will immediately terminate.
In the event that a user or administrator revokes access to a property, there may be subsequent changes made to the IDP-stored user record to help inform other connected customer systems of the change. For example, in the case of Akamai Identity Cloud, user records that are revoked in Consumer Access Control will also have any client entries related to the requesting client id removed from the user record.
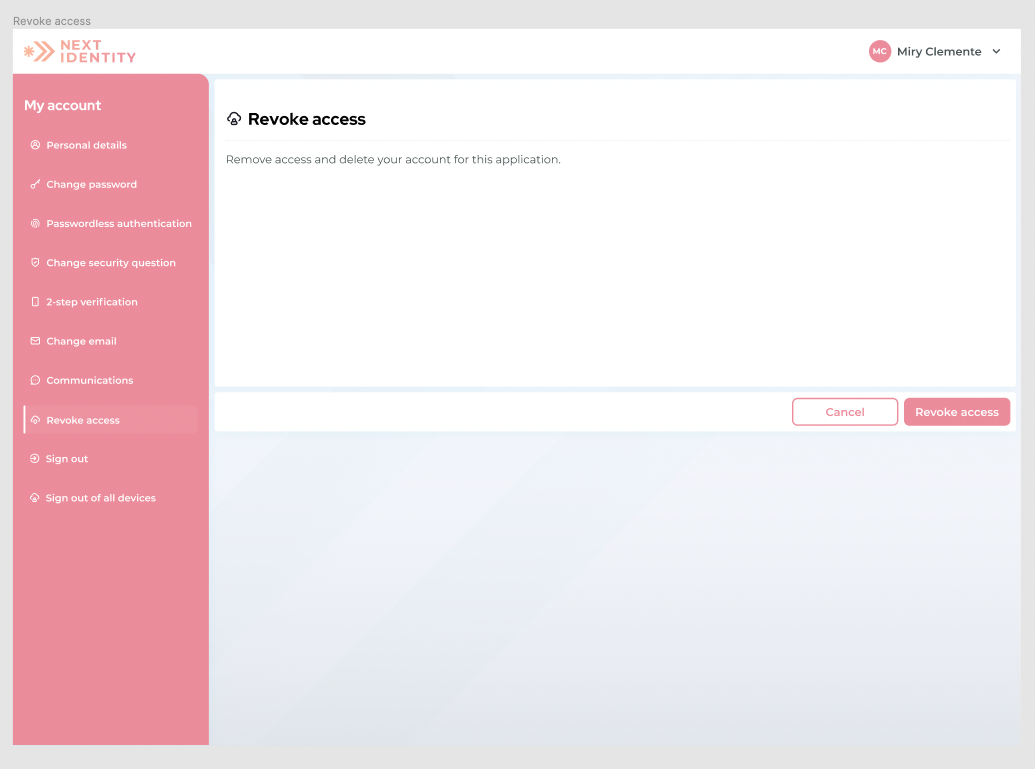
Revoke access menu.
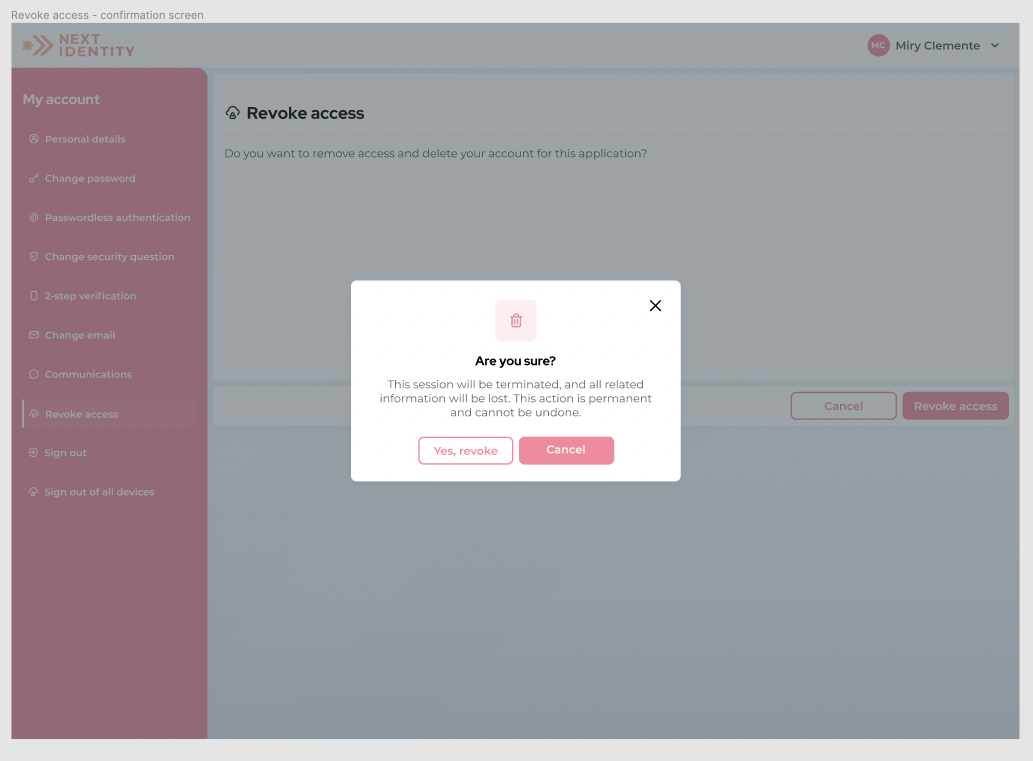
Revoke access confirmation pop-up menu.
Note on the Revoke access optionThis revoke access option is available in the hosted journeys but may require configuration to show up for your end users. Please contact your onboarding consultant if you would like to have this configured for your end users.
Managing consumer access via API
Access status for an end user can also be done via API to support an API-based integration.
For this method, please see our documentation on the property-access endpoint.
Reminder on management via API callManagement via API call requires a token delegation service and a confidential API client type.
Managing consumer access from customer support or admin
For the application admin teams, end-user access status can be checked and can be revoked if needed. For example, in a situation where the end-user has requested to be removed through an alternate channel, like by requesting account revocation through a call to customer support.
For this method, please see our documentation on the property-access endpoint.
Reminder on management via API callManagement via API call requires a token delegation service and a confidential API client type.
How does consumer access control handle multiple property associations?
A consumer who exists in the data store has the right to revoke their account from an application.
However, a user account may be associated with multiple applications within one organization. Revocation from one sub-brand or property does not necessarily mean the user record should be deleted altogether.
With the consumer access control service, when a user requests to be revoked from a specific application, their account is checked to see if they have been granted access to more than one property.
If the user is active in multiple applications, their account is not completely deleted from the organization database. Instead, it is revoked from only the requested property.
If the user has only been active with one application or has previously revoked access from all but the current application, the record will be deleted during that final revocation.
What happens to a user who has revoked access from a property and tries to authenticate again?
If an end-user has revoked access to a property but then tries to authenticate with an application belonging to that property, the user will be denied immediate entry but given the opportunity to re-grant access.
For the hosted journeys, the user will be prompted to consent to granting access again to that specific application, the hosted journeys screen will also display the links to the Terms and Conditions and the Privacy Policy if applicable.
- If a user selects the Deny button, they are logged off and returned to the login page.
- If a user selects the Allow button, the service will update the user record to reflect the new “allow” status for access, and the user will be able to complete sign-in.
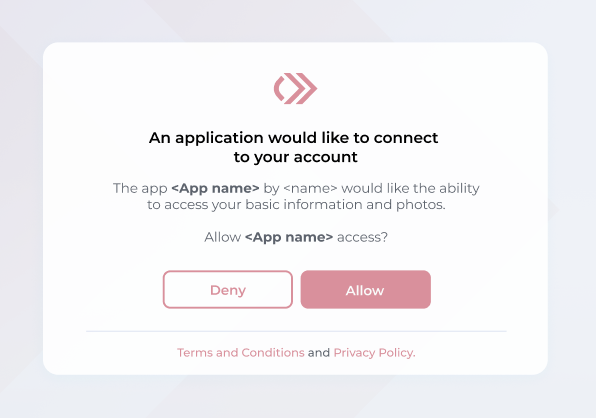
Allow an application to connect to your account.
Updated 9 months ago
