Secret Rotation
Learn to manage and rotate secrets using the Next Identity Console with this user-friendly guide.
This feature helps address security vulnerabilities arising from compromised or stolen secrets, improving the resolution process for such incidents. The Secret Rotation feature allows you to initiate and oversee secret rotations, confirm the success of these operations, and track the history of past rotations.
Before rotating your application's secret, we highly recommend you consult with your Next Identity Consultant. Since secrets function like passwords for API calls, they must be handled with the highest level of confidentiality.
Importance of Regular Secret Rotation
Regular rotation of secrets plays a crucial role in maintaining a secure digital environment. This best practice can be likened to changing the locks on a door periodically - even if a secret was stolen, it won't provide access for long. Here are some reasons why regular secret rotation is so important:
- Limiting Unauthorized Access: If an unauthorized person manages to compromise a secret, they can access the protected system or data until the secret is changed. Regular secret rotation ensures the compromised secret will be made invalid after a limited period, thus reducing the time window for unauthorized access.
- Staying Ahead of Brute Force Attacks: Brute force attacks, where attackers try every possible secret until they find the correct one, are a common security threat. Regular secret rotation helps to stay one step ahead of such attempts, as the secret may be changed before the attacker succeeds in guessing it.
- Mitigating Risks from Insider Threats: Even trusted insiders can threaten system security. Regular secret rotation mitigates the risk of insider threats by ensuring that even if an employee leaves the organization or changes roles, any secrets they had access to will soon be invalid.
- Maintaining Regulatory Compliance: Many industry regulations and data protection laws require periodic secret rotation. Regularly rotating your secrets helps ensure compliance with these requirements.
- Reducing Impact of Human Error: Mistakes happen. Secrets can be unintentionally shared, leaked, or exposed. By regularly changing secrets, the potential damage from such human errors can be reduced.
While regular secret rotation is a crucial aspect of security, it's important to remember that it's just one part of a comprehensive security plan. Other practices, such as enforcing strong access controls, maintaining good security hygiene, and monitoring system activity, are also necessary for maintaining a secure system.
Rotating a Secret
The steps to rotate a secret differ slightly between Service Management View and Application Management View.
In Service Management View
- Step 1: Under 'Operate > Inventory,' select the client you want to rotate the secret.
In the 'Client Details' screen, navigate to the 'Credentials' tab.
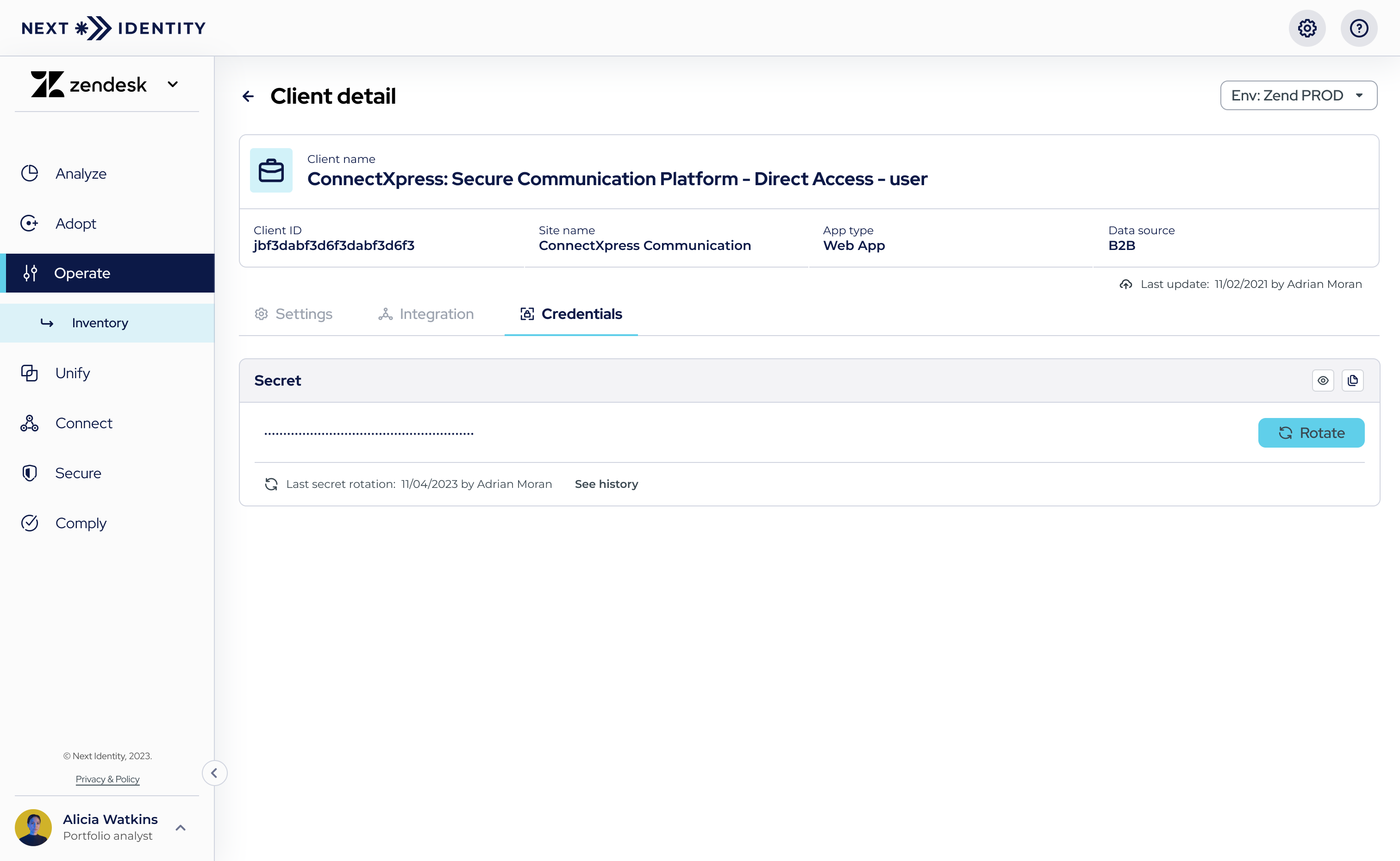
Navigating to the 'Rotate' button in the 'Credentials' tab to initiate secret rotation.
- Step 2: The current secret and the date of its last rotation are displayed on this page.
Select the 'Rotate' button to initiate a new secret rotation. - Step 3: The secret rotation process will start, and a confirmation dialog will appear, allowing you to confirm the environment in which you are rotating the secret.
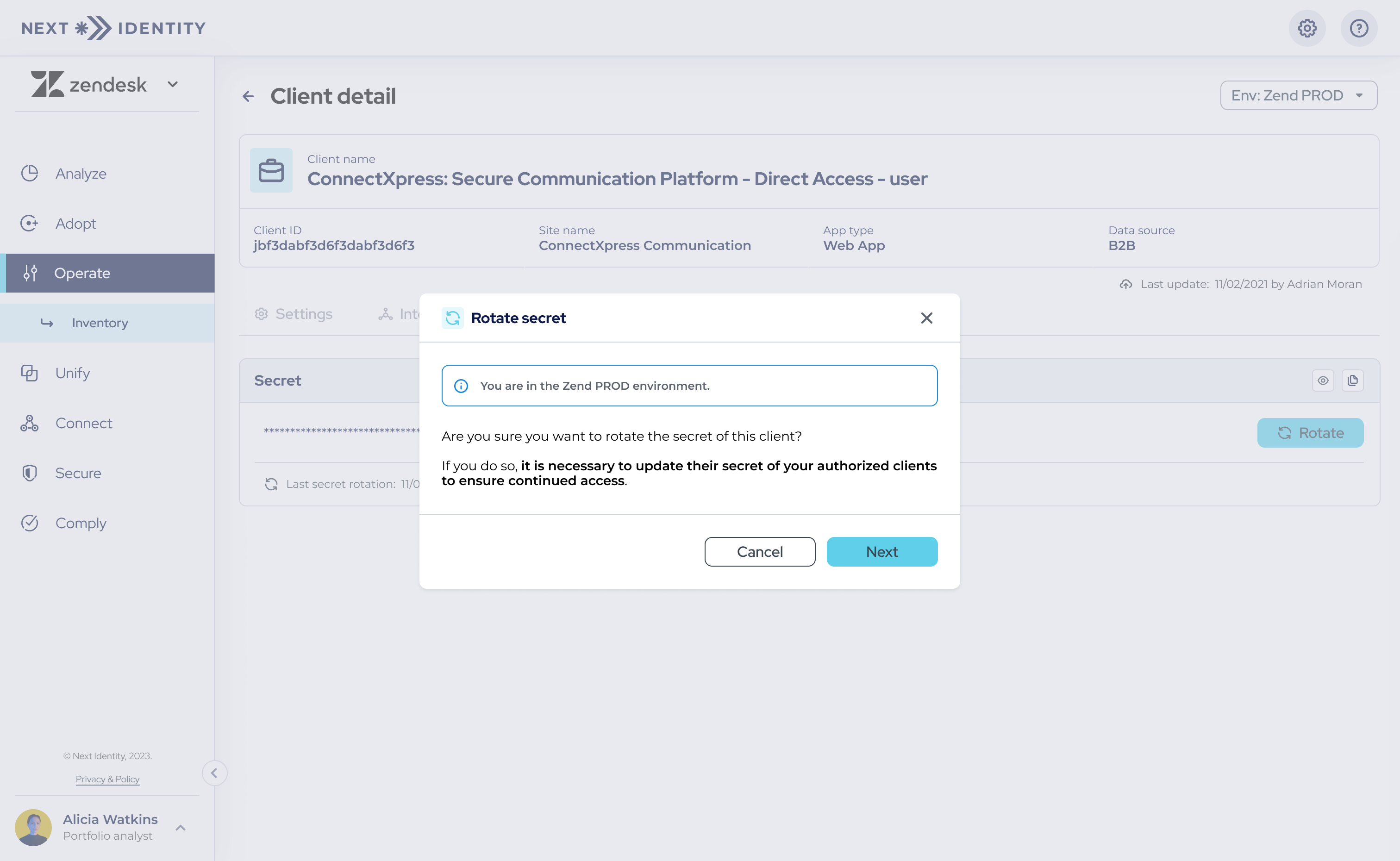
A confirmation dialog for verifying the environment during secret rotation.
- Step 4: Once you confirm your intention to proceed, choose a transition period during which the old secret remains active. This can be anywhere from immediate deactivation (0 hours) to a maximum of one week (168 hours).
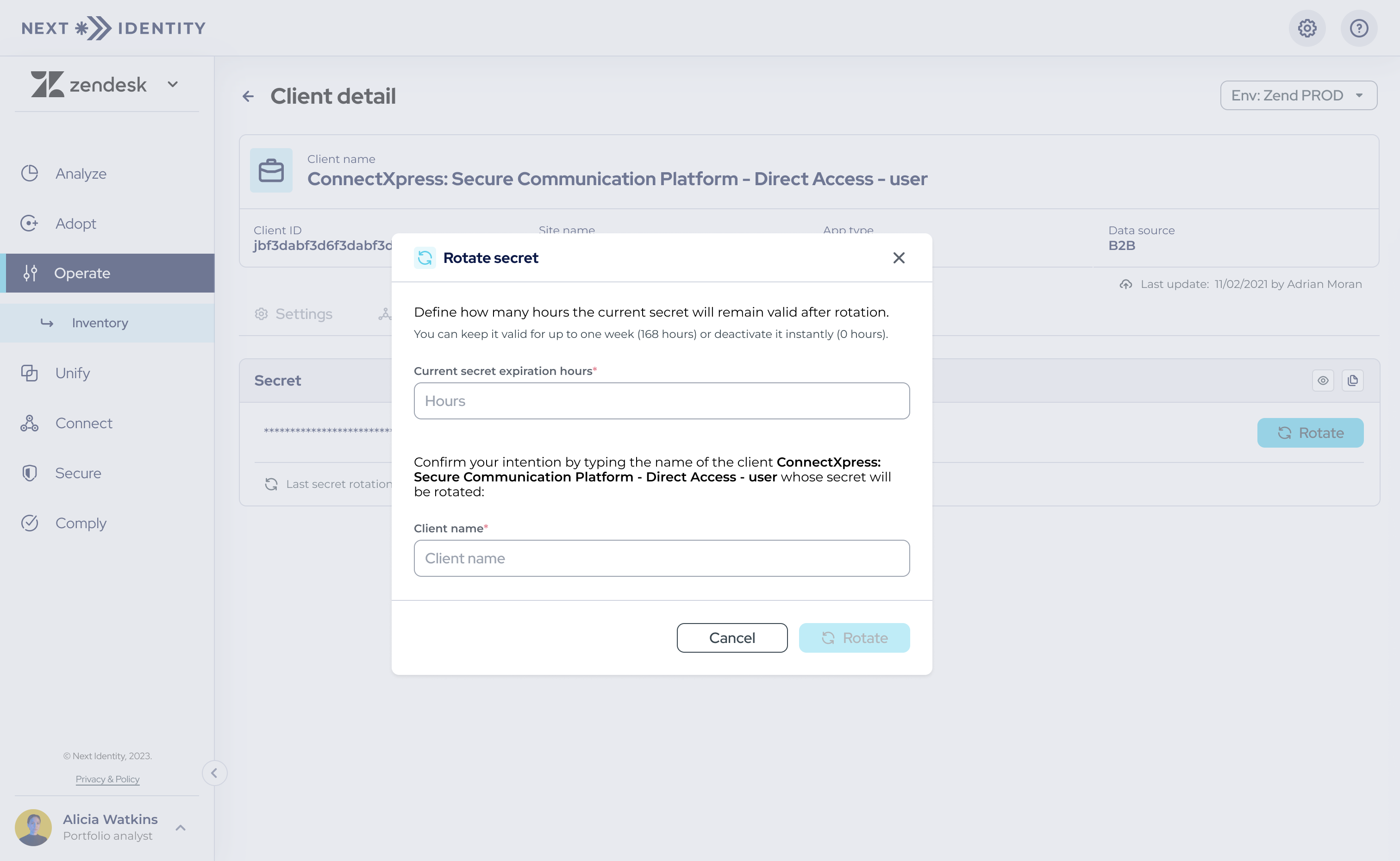
Setting up a transition period for the old secret during the rotation process.
- Step 5: Confirm your intention to rotate the secret by entering the client's name. Once confirmed, a new secret will be generated and displayed on the 'Credentials' tab but will be obscured for security purposes.
You will also see a disclaimer below the secret field, indicating when the previous secret will expire.
To verify the new secret, toggle its visibility by selecting the 'eye' icon.
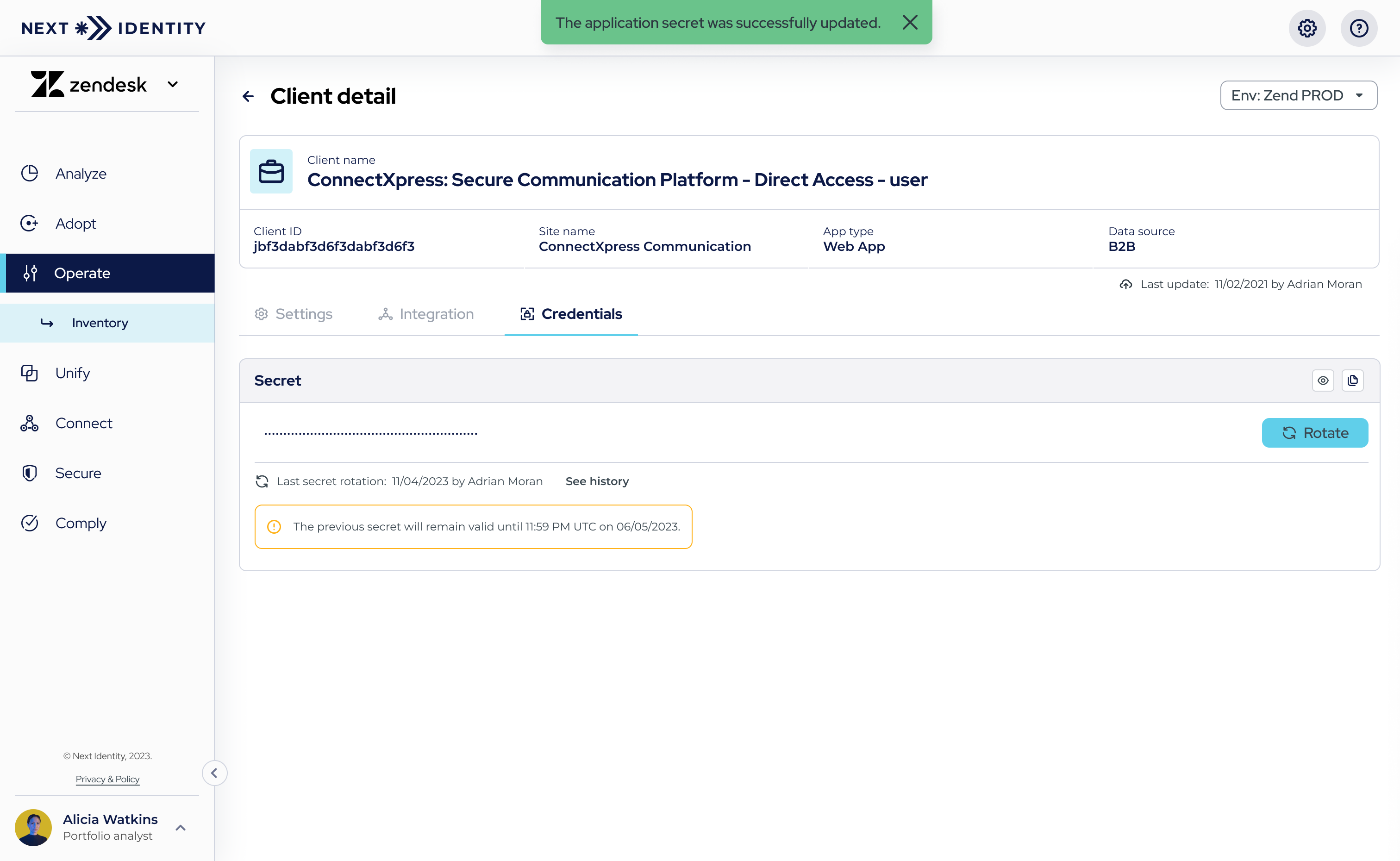
New and old secrets during the transition period.
In Application Management View
- Step 1: Under 'Operate > Clients,' select the client whose secret you want to rotate.
In the 'Client Details' screen, navigate to the environment tab where you want to rotate the secret.
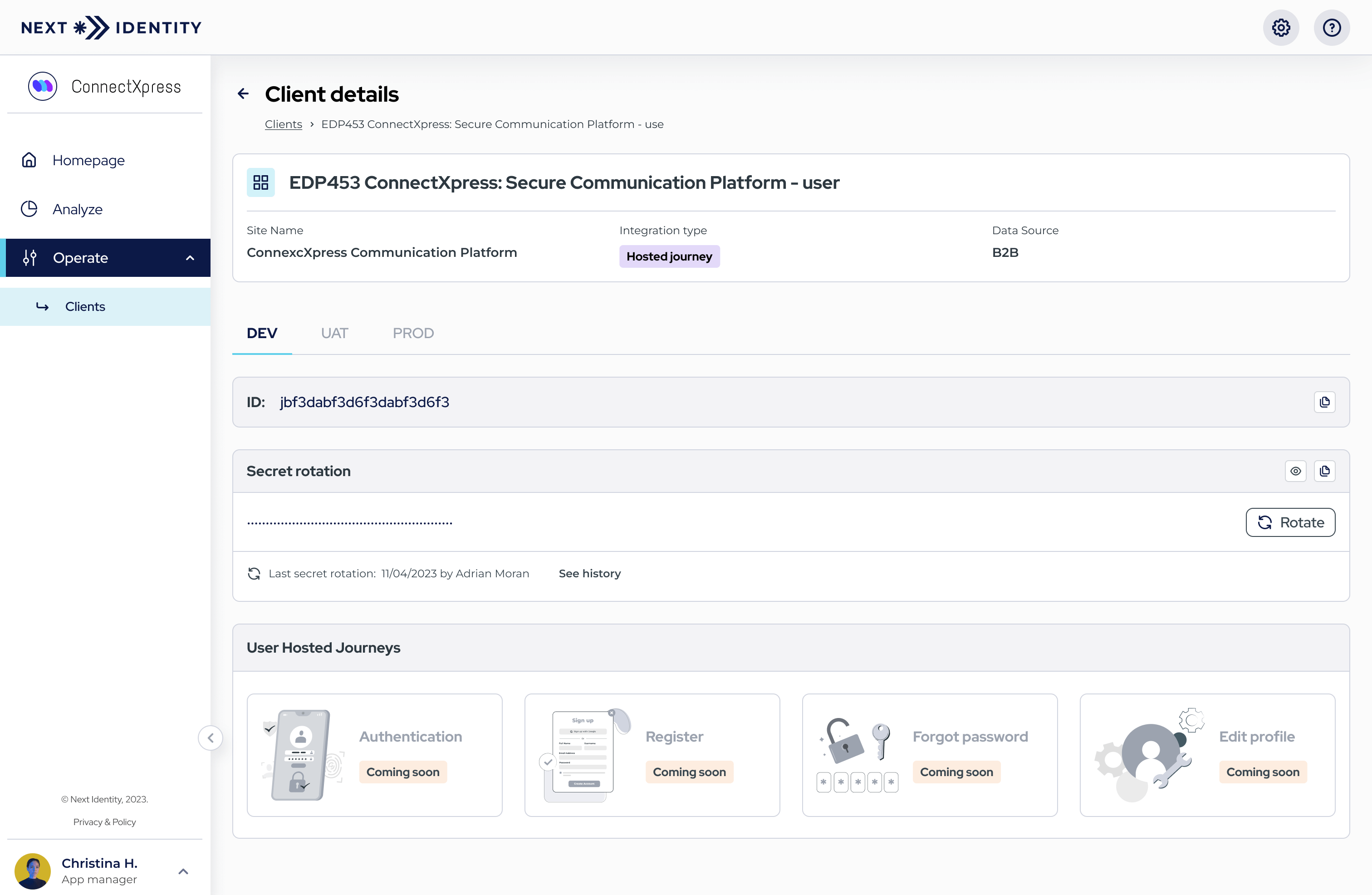
Navigating to the 'Rotate' button in the desired environment tab to initiate secret rotation.
- Step 2 to 5: Follow the same procedure as in Service Management View.
- Secrets can be rotated as often as needed.
- Throughout the transition period, both the old and new secrets are valid and can be used.
Viewing the Secret Rotation History
The steps to view secret rotation history also differ slightly between the two views:
In Service Management View
- Step 1: Under 'Operate > Inventory,' select the client you want to see its secret rotation history.
In the 'Client Details' screen, navigate to the 'Credentials' tab. - Step 2: The 'Secret Rotation History' option will be available if there have been prior secret rotations. The table will include the following details: secret (which can be hidden or revealed), the person who initiated the rotation, rotation date, expiration date, and actions available.
This table can be sorted by various parameters (except for 'Secret' and 'Action') and is arranged by default to show the most recent rotations at the top.
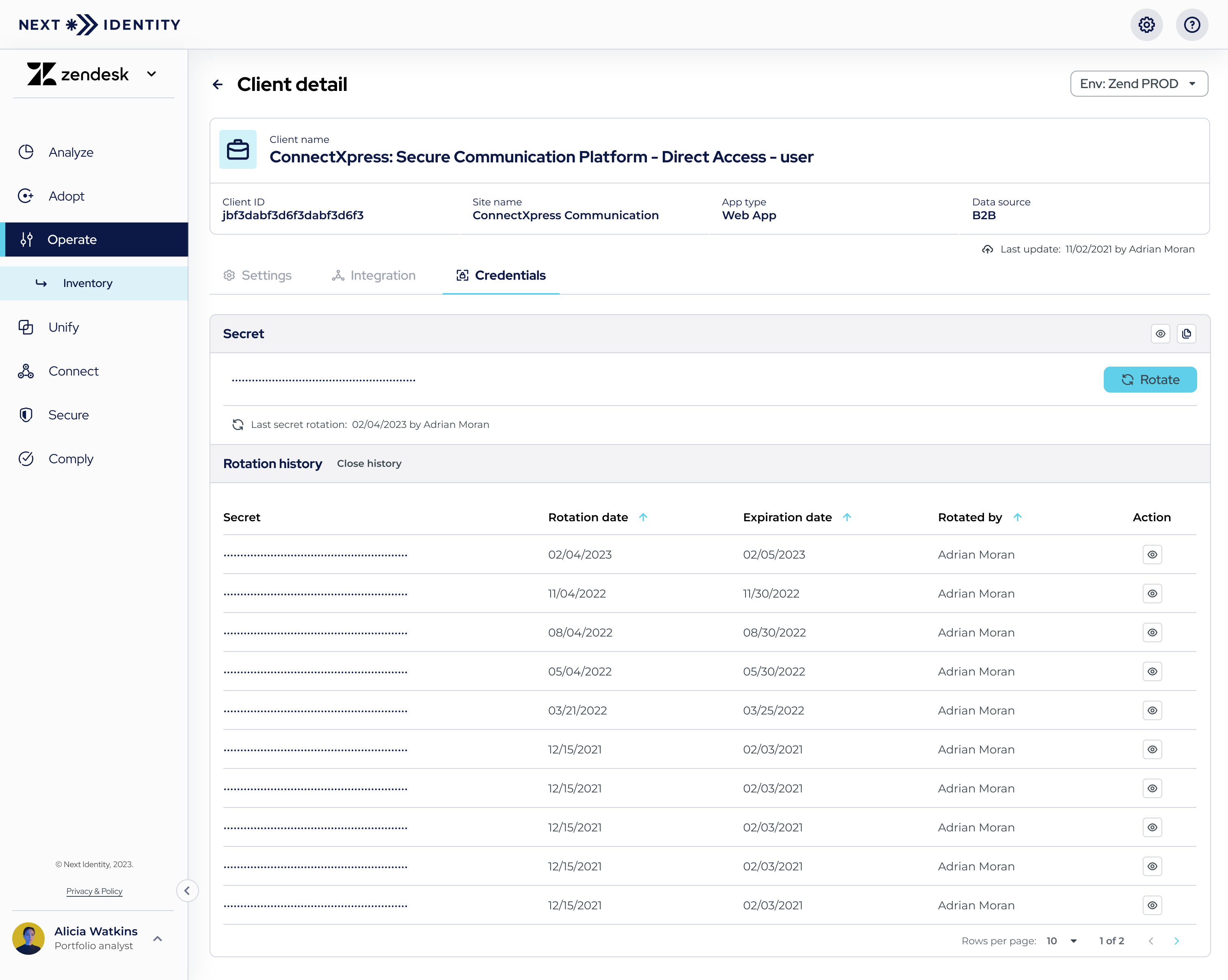
Secret Rotation History
In Application Management View
- Step 1: Under 'Operate > Clients,' select the client whose secret rotation history you want to view.
In the 'Client Details' screen, navigate to the environment tab where the secret resides. - Step 2: Follow the same procedure as in Service Management View.
Roles & Permissions
Access to the "Secret Rotation" feature and its rotation history is determined by user roles and permissions. Different roles have varying levels of access to rotate secrets, view them, and review the rotation history. For detailed information on available roles and their permissions, please refer to the Roles page .
Collaborate with your Next Identity consultant to ensure that the appropriate roles are assigned to the users who need access to these features. For further assistance, please reach out to your Next Identity consultant.
Always Rotate Secrets Using the Next Identity Console
To ensure your applications' security, functionality, and seamless integration, it's imperative to use the "Secret Rotation" feature within the Next Identity Console for all secret rotations. Here's why:
-
Seamless Integration: The feature is designed to work harmoniously with all integrated applications. Rotating secrets outside of this feature can disrupt this integration.
-
Potential Disruptions: Directly rotating a secret on an external IDP can break the feature's functionality for that specific application, leading to unexpected issues and potential security vulnerabilities.
-
Support Limitations: While our support team is always here to help, addressing issues stemming from external rotations can be complex and time-consuming.
Benefits of Adhering to Next Identity's Feature:
- Safety and Security: Our feature ensures that secret rotations are conducted securely, minimizing the risk of unauthorized access or breaches.
- History Tracking: All rotations done through the Next Identity Console are logged, facilitating easy tracking and auditing.
- Consistency: Using the feature guarantees consistency across all applications, reducing the risk of errors or oversights.
For optimal experience and security, always rotate secrets through the Next Identity Console.
Frequently Asked Questions (FAQs)
Q: Why should I always use the Next Identity Console for secret rotations?
A: Using the Next Identity console ensures seamless integration, security, and consistency across all applications. Rotating secrets outside of this feature can lead to disruptions, potential security vulnerabilities, and complex support issues.
Q: What happens if I rotate secrets outside the Next Identity Console?
A: Rotating secrets outside the console can disrupt the feature's functionality for the specific application and lead to unexpected issues. We strongly recommend always using the Console for all secret rotations to ensure optimal security and functionality.
Q: How often should I rotate my secrets?
A: While the frequency of secret rotation can vary depending on your application's specific needs and the sensitivity of your data, a common practice is to rotate secrets every 90 days.
Q: What happens to the old secret once a new one is created?
A: Your old secret remains active for a transition period once a new one is created. This can range from immediate deactivation (0 hours) to a maximum of one week (168 hours). Both the old and new secrets can be used during this transition period.
Q: How do I confirm the success of a secret rotation?
A: After a successful rotation, the newly generated secret will be updated and displayed in the "Secret Rotation" feature while obscured. To verify the new secret, you can toggle its visibility by clicking on the 'eye' icon.
Q: Can I view my past secrets?
A: If you have the appropriate permissions, you can access the "Secret Rotation" feature to view its rotation history. This history provides details about each secret, including who rotated it and the date of rotation.
Q: Who can initiate a secret rotation?
A: The ability to rotate a secret is determined by user permissions. Collaborate with your Next Identity consultant to specify which roles or users have this permission.
Updated 9 months ago
